Defense Against AI
Real vs. Fake
Let's start with what is real and what is fake.
At InReality, by real digital content we mean content that is created by a sensor, on a physical device, that objectively represents reality.
By fake content we mean any content that has been digitally manipulated, photoshopped, AI edited or even entirely created by generative AI.
InReality creates technologies for defending real digital content. We design systems for creating real content, sending real content and verifying real content. Safeguarding the journey from camera chip, across the internet, to the screen on your smartphone.




Defense against AI
For our mission we need a different technology than AI: cryptography
Right now AI invades pretty much all industries with surprising capabilities, performing tasks we didn't think AI could do. But cryptography is different: we have good mathematical reason to believe that AI will NEVER break cryptographic security. This make cryptography the ideal tool for AI defenses
How do we prove reality?
Let us put a cryptographic key as close to a camera sensor as possible. When the camera takes a photo it cryptographically signs the photo at the point-of-creation. Nobody can produce any content on the behalf of the camera, without stealing this key!
The closer we can get the cryptographic key to the camera sensor the more secure our system gets. By publishing a list of cameras and their public keys, we can check the signatures of their photos.
If a photo has a matching signature from a known camera, we use that as proof-of-reality
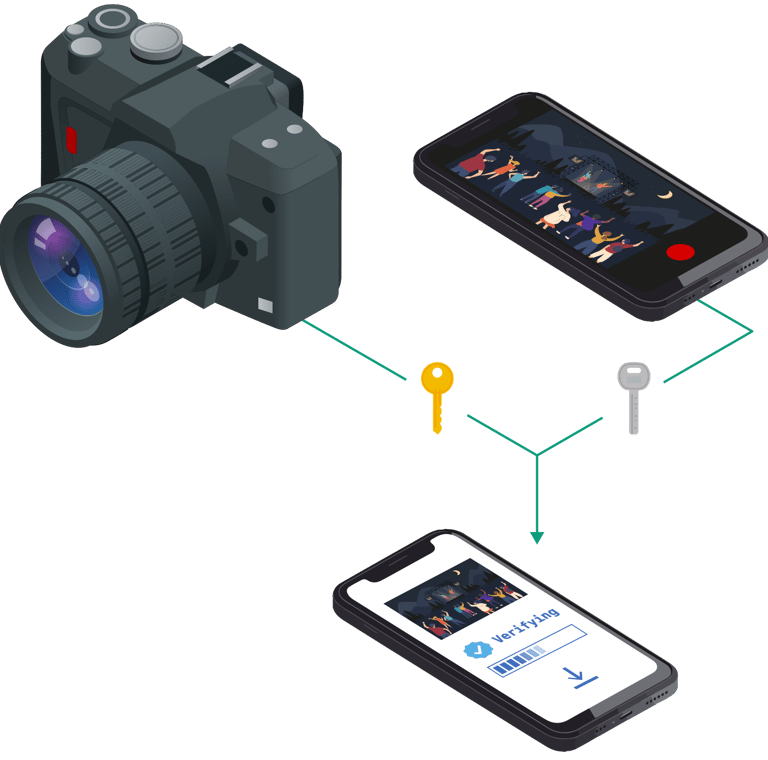
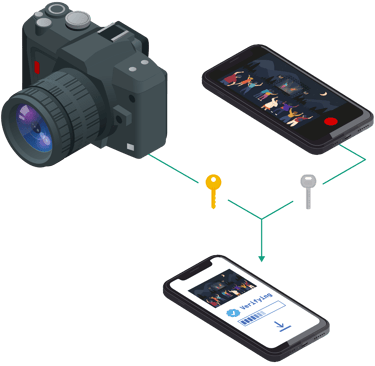


Photo's augmented with origin
The signature is stored inside the photo using a standard called C2PA - this way you do not have to handle complicated data, but simply open the photo with our app or another compatible program.
InReality is a contributing member of the C2PA and hope to help the C2PA community grow 😁
We help create a future where all devices will have cryptographic keys to prove their actions!
The Technology Problem
We imagine a world where every camera chip has a private key (as mentioned above).
Similarly does every microphone, GPS receiver, fingerprint scanner, facial recognition sensor and so on, for all the data our devices can collect. Every CPU/motherboard will have a key for combining sensor data into useful content.
Users will biometrically sign their content, using many different keys: for their job, their bank, their many social networks and so on.
Therefore, a full defense needs tens to hundreds of BILLIONS of keys
If you wish to verify some content, then you need to know all these keys - which is practically impossible.


InReality
We provide the network layer that allows your phone to check thousand of cryptographic signatures in the seconds that you scroll through content, while allowing everyone to sign everything they create.
Our technology is an alternative to blockchain-based solutions and provide the mass scalability that the ultimate AI defense requires